CDSA
M&E Journal: Strengthening Digital Content Workflow and Systems Security
Story Highlights
By Blake White and Richard Delia, Cognizant Business Consulting’s Communications, Media & Technology Practice –
No technology can secure content that the people involved have not committed to securing. In our experience, many people who are directly involved with processing content don’t seem to grasp the value or importance of securing it, nor do they clearly understand the processes or technologies to properly secure it.
Compounding the problem, content has different values at different moments in time. As a result, the people involved need to understand the characteristics of a high-value vs. a low-value asset, as well as the degree of protection technology and processes that should be applied to each.
Staff, vendors and any other stakeholders in the content supply chain need to be better educated and trained on the value of content assets, and the ability to apply a value-based approach to content protection processes and technologies. Without a solid understanding and full adoption of these processes, content will be at risk—and no amount of technology or documented procedures could overcome that vulnerability.
Examine your organizational security posture: Organizations should take a structured approach to assessing their overall content security posture against industry standards and practices, such as those of the Content Delivery and Security Association (CDSA) or the Motion Picture Association of America (MPAA). This includes assessing internal security policies, processes and controls of the content lifecycle against CDSA standards and controls.
The CDSA Content Protection and Security Standard (revised February 2016) includes seven sections, 53 sub-sections and 221 requirements intended to provide guidelines for content protection. Although some sections may not seem to explicitly apply to content security, these guidelines are very important because they provide critical underpinning policies that higher-level content protection technologies and practices rely upon to ensure effective overall content security.
Figure 1: To examine their organizational compliance with the CDSA and/or the MPAA, organizations need to collect, document and validate information across the entire production chain. This process includes interviewing staff and vendors, collecting system configurations and architecture, and reviewing existing policies, procedures and documentation related to security of the media chain.
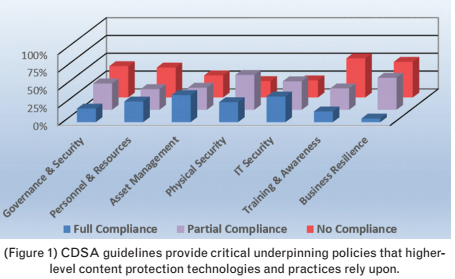 It is important to note that, depending on the maturity of the organization, the collection phase can require a significant amount of work. It is also recommended to obtain an independent technical analysis of your existing security posture to ensure impartiality.
It is important to note that, depending on the maturity of the organization, the collection phase can require a significant amount of work. It is also recommended to obtain an independent technical analysis of your existing security posture to ensure impartiality.
The next step is to contrast and compare how well the organization’s workflows, security practices and content systems comply with the CDSA/MPAA’s recommended practices overall. This analysis also includes compliance and risk scoring, as well as gap identification and mitigation steps.
Such an analysis often reveals risks associated with content repository remediation, access control deficiencies, system upgrades, custom-developed systems, hardening of externally-facing and consumer-facing applications, use of unapproved tools and processes for screeners, and the need for cultural change towards content security.
This information is used to determine the degree of the organization’s compliance with existing standards, which can be helpful for building a remediation roadmap.
Remediation planning and costs
Using the security posture analysis, organizations can then build the remediation roadmap. (Figure 2). This entails the need to prioritize the identified security risks and build an overall project plan (tasks, schedule, resource needs, costs, management, etc.). An important factor in determining the success of the remediation plan is the value associated with the content itself.
Organizations that have not performed an adequate formal assessment of the financial value associated with their content cannot accurately identify or prioritize security risks when undertaking remediation planning.
Plan and cost estimates are based on a typical sourced-services model. One likely exception to this is in custom code development, where internal staff members are expected to dedicate some of their time to the remediation process.
Rather than relying solely on the traditional ROI-based assessment, a recommended practice is to apply a relative cost profile to each remediation project, which includes a risk dimension and a projected timeline. The cost profile is divided into a set of ranges—minimal, moderate, significant and strategic—each of which represents a projected financial cost.
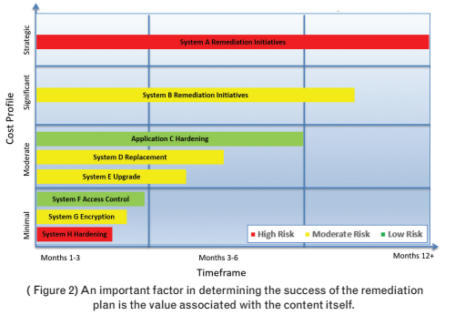 A timeline in the three-, six- and over-12-month horizons is also applied, as well as a risk profile associated with each project.
A timeline in the three-, six- and over-12-month horizons is also applied, as well as a risk profile associated with each project.
All these factors help identify, at a glance, the cost, time and risk levels of all remediation projects. This information can then be used for budgeting, prioritizing, planning and project remediation scheduling.
Actual financial ranges would typically be applied to each cost profile shown; these values are not provided in our sample diagram because they can vary considerably from one organization to another.
Observations and lessons learned
Our experience consulting with media and entertainment companies reveals the following:
*Content valuation is often inadequate or may not have been performed at all. The organization may have little understanding about the value of content at risk, or how different types of content should be treated.
*We often see no overall corporate-level governance structure around content or content security that is agreed upon and adhered to by business unit leaders.
*There may be no authoritative owners of the end-to-end workflows and systems. This leads to a factory-like micro-focus on individual elements of the process, without a strong understanding of the overall risks that might be inherent in the workflows.
*A cavalier attitude toward security rules is not uncommon in some organizations, particularly in departments where there is no penalty for non-compliance. We have seen management fail to enforce policies, penalize for infractions or permit/encourage exceptions to security policies. Over the long term, this puts the company at risk of continued content leakage, as well as penalties associated with contractual content licensing obligations.
*Inordinate trust is often placed in the security of the internal network, which leads to a false sense of security and the perception that there is little need to adhere to the proper degree of content security.
*As with many content producers, the cultural value system is often one of “get the content up and out.” As a result, there is often minimal incentive to clean up after airing or publishing. Old versions of shows and links remain active on distribution servers, increasing the risk of occasional mistaken leakage through content mis-identification.
*From a security perspective, disparate internal development efforts that have grown over many years typically do not conform to commercial best practices around platform security, hardening, revocation, renewal, transaction logging, etc.
*The primary product of a M&E company is not software, yet we often see a very large amount of resources dedicated to software development. As these are not ‘software companies’, they sometimes lack the degree of formal best practices that commercial software companies use to ensure strong security of their products.
Strategic recommendations
Protecting content starts with people and effective planning; from there, content protection policies and technologies will be defined and created. To this point, we highlight a set of strategic recommendations that we believe will significantly impact the quality and effectiveness of a content security program:
*Establish an overall corporate governance structure around content and content security that is agreed upon and adhered to by business unit leaders.
*Implement a formal content valuation process across business units and brands to establish a baseline value of the company’s content that may be at risk, as well as a plan for treating different types of content with different levels of content protection.
*Adopt and train developers on software development and communications security best practices that are followed by leading commercial software companies; this is particularly important if your organization is intent on developing its own technology.
*Implement a well-structured education and training program on content security processes and technology, and obtain the necessary resources and support from the organization’s leadership to see these programs to fruition.
*Perform routine assessments of your organization’s content security compliance to ensure adherence over time. Doing so can help organizations contend with constantly changing people, technology and workflows, which often leads to gaps in content security compliance.
Summary
To properly implement a comprehensive content security plan, M&E companies must focus on people, their existing security profile and remediation. Without getting people on-board and trained, you have no security. Without a security profile, you don’t know your level of risk. And without remediation planning and execution, it’s all just talk.
—
Click here to translate this article
Click here to download the complete .PDF version of this article
Click here to download the entire Spring 2017 M&E Journal









